Grouping a Secure Boot Chain
Each boot chain when booted can be verified as a group of secure binaries in its entirety by enabling the partition version information table (PVIT) feature.
The PVIT is a structure, which contains the version and sha512 of each binary loaded in the normal boot flow. After the PVIT is securely loaded and authenticated using its associated Boot Component Header (BCH), each firmware is verified to match its corresponding entry’s sha512 hash value as shown in the following table before execution or consumption of the data. The PVIT structure is passed on to the next stage of boot until the entire chain is verified.
The PVIT structure is defined as follows:
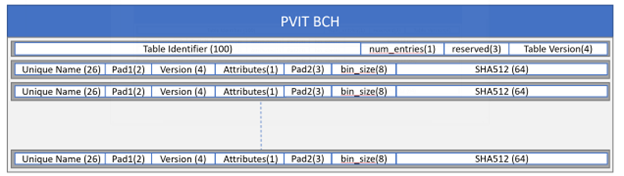
The PVIT feature is enabled in the MB2-BCT by setting the enable_pvit
field and adding the appropriate PVIT partition in the boot chain.
pvit_validate flag.Set pvit_validate=no in
boot_chain_storage.cfg/qnx_gos0_storage.cfg/qnx_update_vm_storage.cfg/qnx_gos1_storage.cfg
for the partition whose PVIT check needs to be disabled.
- psc-bl
- mb1-bct
- mem-bct
- mb2-bootloader
- pva-fw
- mts-mce
- ist-ucode
- bpmp-ist
- ist-config
- fskp-fw
- sc7-fw
- mb2-rf
- bpmp-fw
- bpmp-fw-dtb
- psc-fw
- ccplex-ist-ucode
- tsec-fw
- mb2-applet
- psc-rf
- mce-coverage
- ape-fw
- spe-fw
- rce-fw
- dce-fw
- adsp-fw
- xusb-fw
- fsi-fw
- pva-fw
- secure-os
- kernel (Hypervisor)
- oist-tst-vtr
- plat-misc-cfg
- pt (L3)
- kernel
- kernel-dtb